
One aspect of application design and network architecture which people generally neglect is the fact it depends on teamwork just as significantly like a bodily made architectural job. The modern industry of IT requires massive amounts of people all operating collectively within a hugely coordinated way. When matters go mistaken with all the group, it will ordinarily end up hurting the challenge within the long run. That’s why it is so crucial to use resources such as the IT audit checklist.
The basic use of the IT audit checklist is very uncomplicated. A single will initially should have a basic term processing method installed. Whilst Microsoft Term is the standard, free solutions for example LibreOffice can also be compatible while using the checklist. Right after making certain the required software program is put in, 1 really should download the template from this site. Try to remember where you downloaded it to, after which you can double click on it. Your phrase processor will then progress to open up the checklist. The IT audit checklist is thoroughly usable as it is, but one can also effortlessly edit it to fit one’s requirements.
Samples of IT Security Checklist :
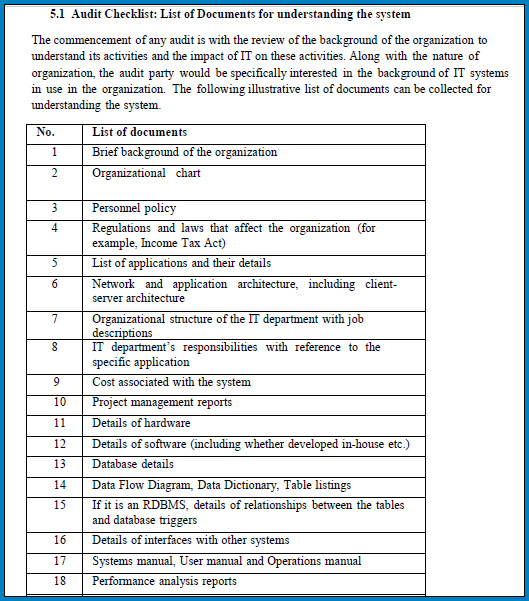

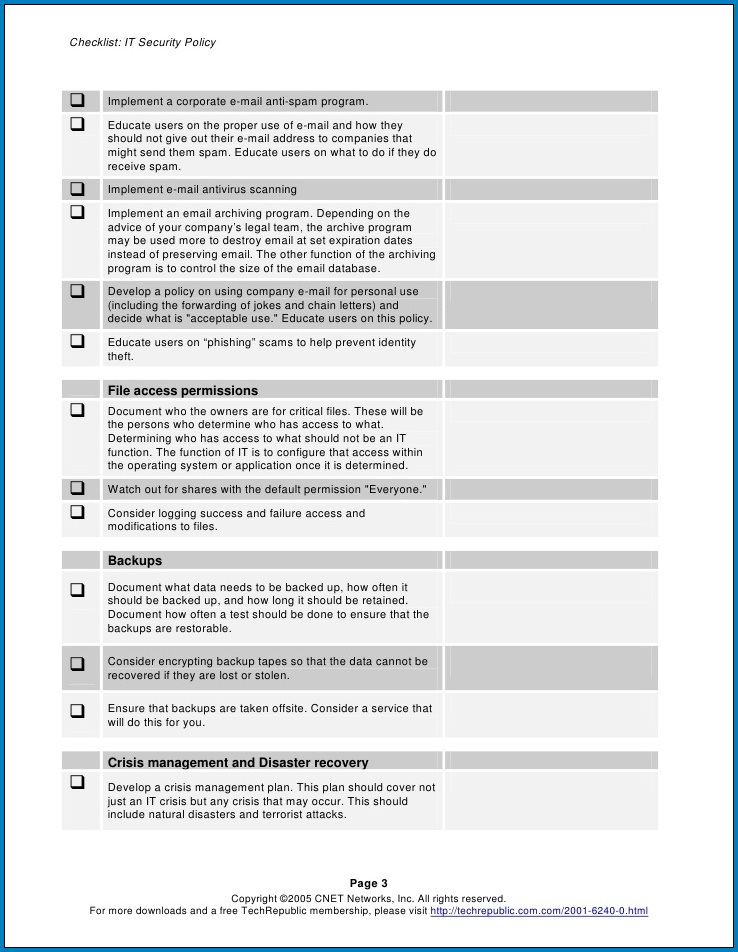

Recommendations for Applying the IT Security Checklist :
- Keep in mind how easy it is actually to customize the template. One particular should really hardly ever be afraid to generate also a lot of changes to it as a way to let it suits your needs.
- Bear in mind all departments want to be associated with the procedure. Each individual department may even have numerous particular person points to contribute which you may perhaps not bear in mind of. After editing the template, one particular must verify with all the head of each office so that you can be sure that everything crucial that you them is to the IT audit checklist.
- Bear in mind to electronically file the IT audit checklist. Paper copies is usually helpful, but digitally saved backups are so conveniently saved that it should always be done.
- Really do not feel you should keep track of every little thing. When the IT audit checklist is shared, such as within a cloud storage program, than diverse departments can separately monitor lots of objects by by themselves.
IT Security Checklist Template | Excel – download